JWT Token Debugging Made Easy: Online Decoder Helps You Quickly Troubleshoot Authentication Issues
Deep dive into JWT Token debugging pain points and solutions, from quickly viewing Token content to verifying expiration time, from troubleshooting authentication errors to understanding Token structure, helping developers efficiently debug JWT-related issues and improve development efficiency.
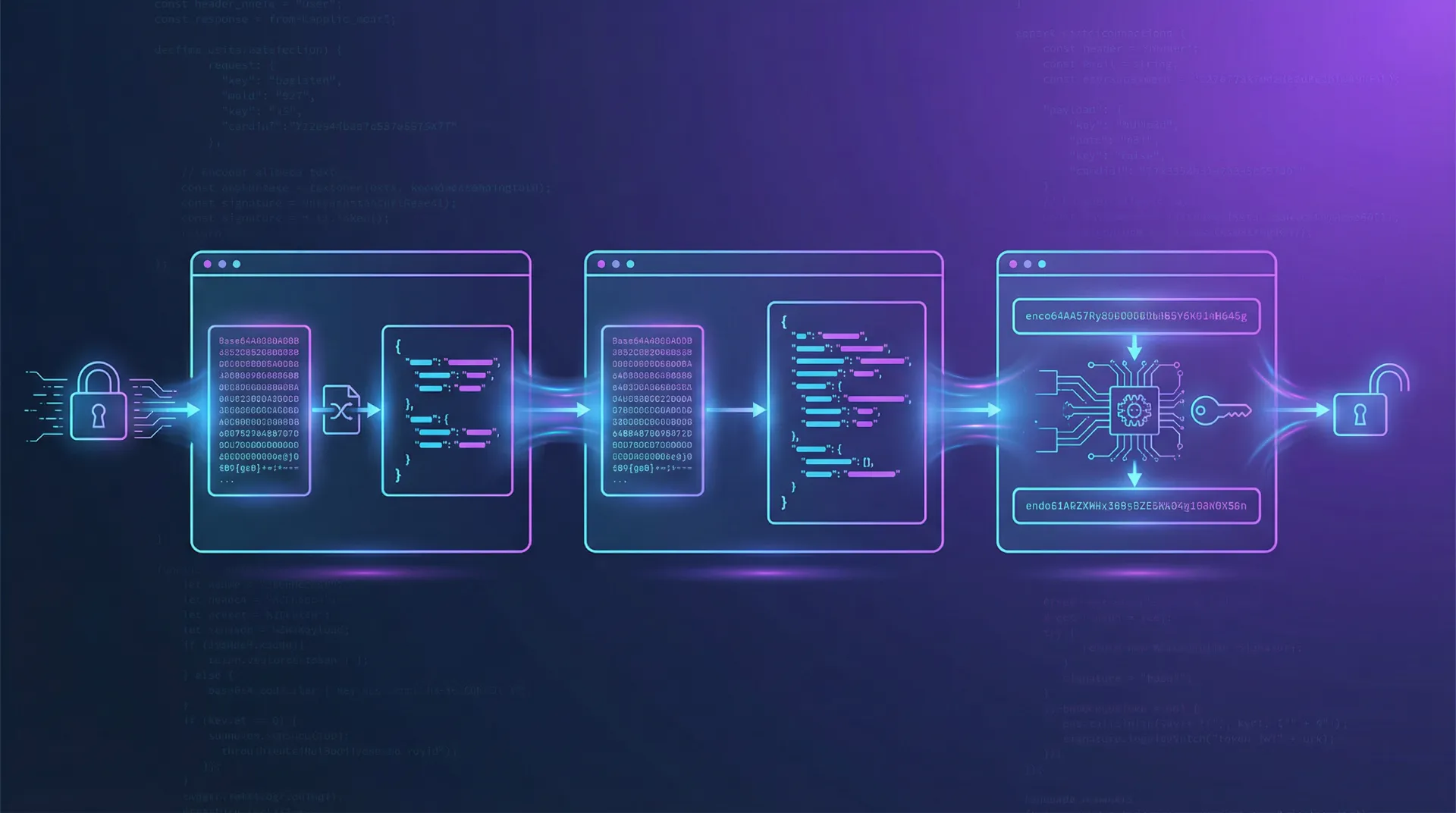
In modern web development, JWT (JSON Web Token) has become the mainstream solution for authentication and authorization. Whether it’s a frontend-backend separated SPA application or inter-service communication in a microservices architecture, JWT plays a crucial role. However, when an API returns a 401 unauthorized error or Token validation fails, developers often need to quickly view the Token’s content to troubleshoot the issue.
JWT Debugging Pain Points: Information Hidden in Base64
A JWT Token consists of three parts: Header, Payload, and Signature, separated by dots (.). Although the Payload part contains key data such as user information, permissions, and expiration time, this information is Base64 URL encoded, making it appear as an incomprehensible string when viewed directly.
Common pain points include:
- Unable to quickly view Token content: When an API returns an authentication error, you need to know what information is actually in the Token. Is it expired? Insufficient permissions? Or is there a Token format issue?
- Requires installing additional tools: The traditional approach is to use command-line tools (such as
jwt-cli) or write scripts to decode, but these require installing dependencies in the local environment, which is too cumbersome for temporary debugging. - Difficult to verify expiration time: The
exp(expiration time) field in the Token is a Unix timestamp, requiring manual conversion to know the specific expiration time, which is very inconvenient. - Low troubleshooting efficiency: When debugging authentication issues, you often need to repeatedly view Token content. If you use command-line tools every time, it will significantly impact development efficiency.
Solution: Online JWT Decoder
This is why we need to use the JWT Online Decoder/Validator. As a professional JWT debugging tool, it helps you quickly view and verify various components of JWT Tokens without installing any third-party libraries or command-line tools.
Core Features Explained
1. Quick Decode Header and Payload
The tool supports automatic recognition of JWT Token format. Whether it’s a complete Token or a Token with a Bearer prefix, it can be correctly parsed. After decoding, the tool displays the Header and Payload content in formatted JSON, allowing you to see at a glance:
- Header information: Token type (typ), encryption algorithm (alg), etc.
- Payload information: User ID (sub), issuer (iss), audience (aud), expiration time (exp), issued time (iat) and other standard claims, as well as any custom claims
2. Intelligent Extraction of Token Key Information
The tool automatically extracts key information from the Payload and displays it in an easy-to-read format:
- Expiration time: Automatically converts Unix timestamp to local time and shows whether it has expired
- Issued time: Displays the Token’s issued time, helping to determine the Token’s age
- Issuer (iss): Shows the Token’s issuer for verifying Token source
- Audience (aud): Shows the Token’s target audience for verifying Token usage scenarios
- Encryption algorithm: Shows the signature algorithm used by the Token (such as HS256, RS256, etc.)
3. Verify Token Format and Basic Validity
The tool checks whether the Token’s basic format is correct (whether it contains three parts, whether each part is valid) and verifies:
- Whether the Token format is correct (three parts separated by dots)
- Whether Header and Payload can be correctly decoded to JSON
- Whether the expiration time is valid (if expired, it will be clearly marked)
4. One-Click Copy Function
The decoded Header, Payload, and Signature can all be copied with one click, making it convenient for you to use in code or documentation.
Real-World Application Scenarios
Scenario 1: API Authentication Error Troubleshooting
When your frontend application calls an API and returns a 401 error, you can:
- Copy the JWT Token from the browser’s developer tools
- Paste it into the JWT decoder
- Immediately check whether the Token is expired, whether user information is correct, and whether permissions are sufficient
Scenario 2: Verify Token Expiration Time
During development, you may encounter the problem “The Token hasn’t expired yet, why is validation failing?” Using the decoder, you can:
- View the Token’s
expfield to confirm the expiration time - Check whether the server time is consistent with the Token expiration time
- Verify whether the Token’s
iat(issued time) is reasonable
Scenario 3: Understand JWT Structure
For beginners, the JWT structure may be abstract. Using the decoder, you can:
- Intuitively see the content of the three parts: Header, Payload, and Signature
- Understand the meaning of standard claims (such as
exp,iat,iss, etc.) - Learn how to add custom claims to the Payload
Scenario 4: Security Audit
When conducting security audits, you may need to check:
- Whether the Token contains sensitive information (such as passwords, keys, etc.)
- Whether the Token’s expiration time setting is reasonable
- Whether the Token’s signature algorithm is secure
Why Choose an Online Tool?
Compared to installing command-line tools or writing scripts, online JWT decoders have the following advantages:
- No installation required: Open the browser and use it immediately, no environment configuration needed
- Cross-platform: Works on Windows, macOS, and Linux
- Instant availability: No need to wait for dependency installation, start debugging immediately
- Privacy and security: All processing is done locally in the browser, no data is uploaded to the server
Summary
JWT Token debugging should not be an obstacle in the development process. By using the JWT Online Decoder/Validator, you can quickly view Token content, verify expiration time, and troubleshoot authentication issues, spending your time on more valuable development work.
If you frequently need to handle JWT-related development tasks, we recommend bookmarking this tool—it will become a powerful assistant in your debugging toolkit. You can also find more practical development tools in the Developer Tools category.
🚀 Try Related Tools Now:
- 🔑 JWT Online Decoder/Validator - Quickly view and verify JWT Token’s Header, Payload and signature validity
